A few weeks ago, I started receiving tweets and emails from people who claimed that search results for my site were looking more like a pharmacy than a helpful Web resource.
Of course, upon hearing such blasphemy, I immediately opened a new browser tab, looked around to make sure no one was watching, and then started Googling myself…and if you think that is some NC-17 material, wait til you see what my search results looked like:
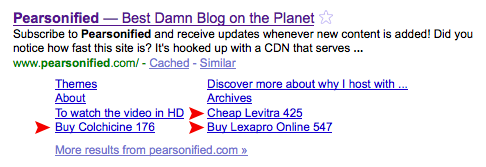
Figure 1. The three red arrows highlight <title> tags that were cloaked by the WordPress pharma hack. Helpful Web guy or reckless pill-slinger? You decide :D
What you don’t see in the picture above is a hacked <title> tag for my home page, but that’s only because I fixed it before realizing I was going to write an article about these shenanigans.
Suffice it to say that, before I caught the hack, my site looked more like the best damn antidepressant resource than the best damn blog on the planet.
Enough of that, though—let’s dig a little deeper into the WordPress pharma hack and see what it’s all about.
What Does the WordPress Pharma Hack Do?
There are three facets of the pharma hack that I find particularly interesting. First, the results of the hack are only visible to search engines, and if your site is hacked, the public-facing portion of it will remain visibly unaffected. In other words, you won’t be able to spot the hack just by viewing the HTML source. The goal of any hack like this is to gain valuable links from high-ranking pages, and these hackers have wisely chosen to disturb the water as little as possible while going about their dirty business.
Second, like other hacks, the pharma hack must place malicious files in your WordPress folders in order to work its evil. However, unlike other hacks that I’ve encountered, the pharma hack disguises a majority of its code and saves it in the WordPress database, thereby making it more difficult to find and eliminate.
The third remarkable aspect of the pharma hack was that it didn’t affect every page of my site. Further, it only targeted the pages of my site that receive the most search traffic. For example, in Figure 1 above, the three hacked titles correspond with the following posts:
- 2 Sure-fire Ways to Make Money Online
- Deal or No Deal: A Statistical Deal
- How Much Should a Web Design Cost?
Interestingly, these three pages contain the most potent and high-ranking keywords on my site. Also, back when I ran AdSense, two of those three pages were the highest earners on the entire site (as far as PPC is concerned, anyway1).
With these key points in mind, let’s answer the original question here: What does this hack do?
The WordPress pharma hack quietly exploits your highest-ranking and most valuable pages by overriding the title tag and by inserting spammy links into the page content. Interestingly, the modified title tag and spammy links are only visible to search engines.
How Does the WordPress Pharma Hack Work?
We know what the pharma hack does, but in order to eliminate it and to prevent attacks like this in the future, we need to know how it does what it does.
Basically, the hack consists of two parts—malicious files in the WordPress plugins folder coupled with encrypted code in the WordPress database. The files in the plugins folder contain code that runs the encrypted code stored in the database. Because of this, the pharma hack is dependent upon these rogue files in the plugins folder.
Typically, hack files contain easily-identifiable PHP functions like eval() and base64_decode(), and although the pharma hack is no exception, there’s one major difference. With the pharma hack, these functions are stored in the WordPress database as strings, and they’re encoded backwards! At runtime, a hack file in the plugins folder pulls these strings from the database, flips ’em, and then runs ’em as functions, and that’s how the deed gets done.
Oh, and remember how I said this hack only targeted my most potent and high-ranking pages? Cleverly, the hack pings Google Blog Search with queries like this one (edit: link removed) to see how many links a particular page has, and then it stores the results in the database. At runtime, the hack uses the number of links to determine which pages to target…
Sneaky bastards :D
How to Remove the WordPress Pharma Hack
Even if you don’t see any symptoms of the pharma hack (like cloaked title tags in search results), your site may still be hacked and therefore completely vulnerable. To know for sure, you’ll have to dig through the two places where the hack is known to romp—your WordPress plugins folder and your WordPress database.
Oh, and before we go any further, let’s get one thing straight—you are running the latest version of WordPress, aren’t you? Good, I knew you were the sensible type :D
Step 1: Remove Hack Files from Your Plugins Directory
Let’s start by examining the WordPress plugins folder for hack files. Using an FTP client, navigate to the /wp-content/plugins directory, and then locate your Akismet folder. I’ve recommended this particular folder as a starting point because I found malicious files stored here on three different sites; however, based on what I’ve learned about the pharma hack, these malicious files could be in the directory of any active plugin. Therefore, in order to do a thorough diagnosis, you should check any plugin that was active at the time your site was hacked.
Using your FTP client, make sure your viewing options are set to show hidden files, and then check to see if any of the following malicious files are located in your Akismet plugin folder:
.akismet.cache.php.akismet.bak.php.akismet.old.phpclass-akismet.phpdb-akismet.php
Ultimately, the important thing to note here is not the filenames themselves, but rather the patterns these names follow.
Items 1–3 are hidden files, and they all exhibit a characteristic naming structure with .cache, .bak, .old, or a similar pseudo-extension in the middle of the filename. Generally, you’ll find two out of three of these files together—one will look like this, and the other will look like this.
Items 4 and 5 share a naming convention, too—they are simply the plugin name (or a truncated version of the full plugin name) prefixed by either class- or db-. If you find a file that matches this convention, its contents should look like this.
Now, when you check other folders, you’ll know what naming patterns to look for when attempting to spot hack files, you sleuth you!
Here’s what one of my infected Akismet folders looked like; note that an uninfected Akismet folder only contains three files (akismet.gif, akismet.php, and readme.txt) and no hidden files:
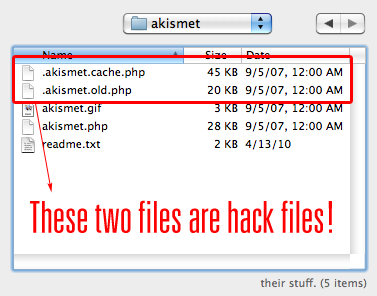
Figure 2. Two hidden files inside the Akismet plugin folder that were planted by the WordPress pharma hack.
If you find infected files, delete them! Doing this will effectively end the pharma hack symptoms and restore your search results, but it’s important to note that your site will still be vulnerable at this point. In order to completely remove all traces of the hack and restore the integrity of your site, you’ll need to dig into your WordPress database to remove some lingering offensive code.
Step 2: Remove Malicious Code from Your WordPress Database
Because this step involves database interaction, it’s crucial that you pay close attention to the instructions outlined here. Also, it’s always a good idea to make a database backup before manually editing anything, so don’t say I didn’t warn ya!
To begin, you’ll need to access phpMyAdmin, which is a program on your server that allows you to view the databases associated with your hosting account. If you’ve never heard of phpMyAdmin and don’t know how to access it, don’t worry—simply contact your Web host, and they’ll be able to help you out here.
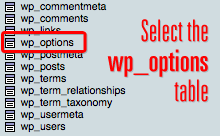
Figure 3. Select the wp_options table in your WordPress database.
Once you’re inside phpMyAdmin, select your active WordPress database from the left side of the page. If you’ve selected the correct database, you’ll notice a new set of links on the left—a collection of tables that look like those shown in Figure 3. From here, click on the wp_options table, and this will allow you to browse the table contents.
Your goal here is simple—you need to delete database entries that contain malicious code. Fortunately, finding the entries you need to delete is a simple job if you use the phpMyAdmin search function, which you can access by clicking the Search tab at the top of the page, as shown in Figure 4:
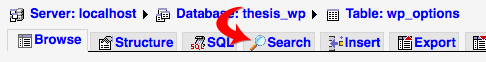
Figure 4. Click on the Search tab to search the wp_options table inside phpMyAdmin.
On the search screen, you’re going to need to search the option_name field (see Figure 5 below) for the following rogue database entries:
wp_check_hashclass_generic_supportwidget_generic_supportftp_credentialsfwprss_%— Attention! In this case, you should delete all matches exceptrss_language,rss_use_excerpt, andrss_excerpt_length(these are legit WordPress database entries).
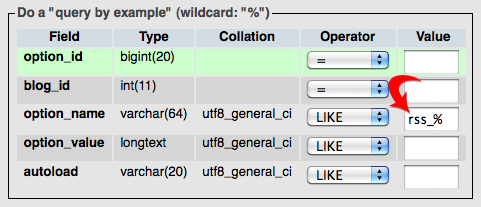
Figure 5. Search the option_name field for malicious database entries from the list above. If you find any of these entries, delete them!
What Next? (And Some Helpful Prevention Tips!)
Now that you’ve successfully removed the WordPress pharma hack, you’re probably wondering what you can do to prevent stuff like this from happening in the future. On that note, I’ve got some good news, and I’ve got some bad news. First up, the bad news…
At this time, there is still one huge unanswered question about the WordPress pharma hack: How in the hell did the hackers manage to get into your server in the first place? I’ve received reports of the pharma hack on a variety of different Web hosts and server configurations, so it’s clear that the main vulnerability extends beyond a single host/server platform. So far, the only common denominator between the sites I’ve examined is that they’re all running WordPress, but even this fact doesn’t mean that WordPress itself is the problem.
Alright, with the bad news out of the way, it’s time for the good news: You can prevent hacks like this in the future. Rather than rehash the information here, I’m going to point you to a fantastic resource on WordPress security tips. From the perspective of someone whose site just got dropped from Google’s index because of the pharma hack (that’s me), you would be wise to follow these simple security suggestions :D
1 For the record, I think AdSense and PPC advertising are terrible ways to make money online for two reasons. First, they sodomize the visual flow of your site by taking up valuable real estate, and second, they simply aren’t as genuine and helpful to mankind as other methods of monetization. For more, read up on the two methods I recommend for making money online. ↩